OAuth 2.0 with Gmail over IMAP for installed applications (DotNetOpenAuth)

OAuth is an open protocol to allow secure API authorization in a simple and standard method from desktop and web applications.
This article describes using OAuth 2.0 to access Gmail IMAP and SMTP servers using .NET IMAP component in installed applications scenario. You can also use OAuth 2.0 for web applications.
DotNetOpenAuth
First download the latest version of DotNetOpenAuth – it’s free, open source library that implements OAuth 2.0: http://www.dotnetopenauth.net
Register Application
Before you can use OAuth 2.0, you must register your application using the Google Developers Console.
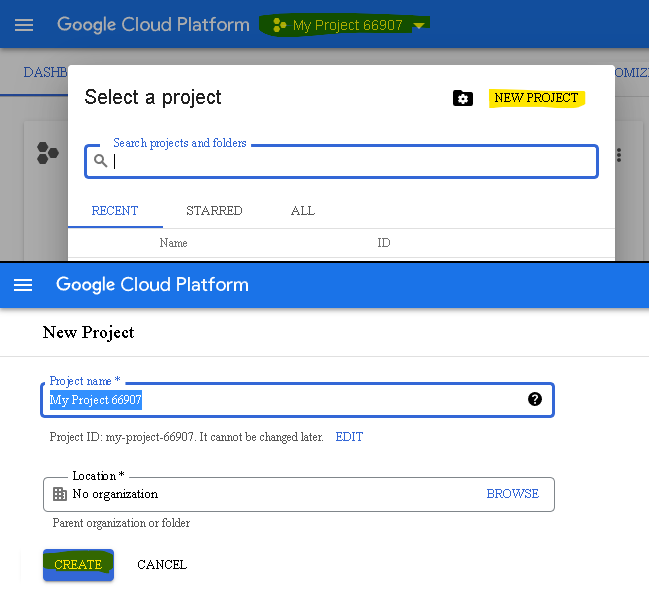
At least product name must be specified:
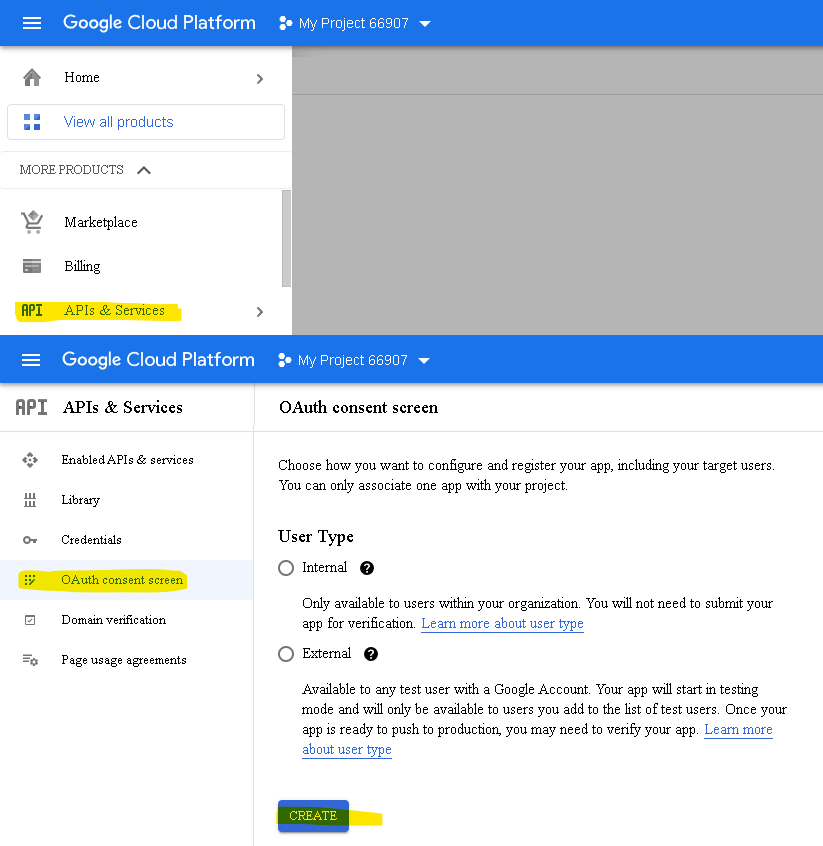
Now create credentials:
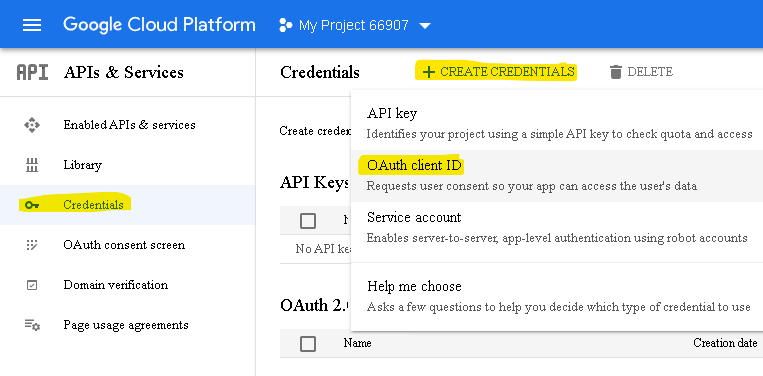
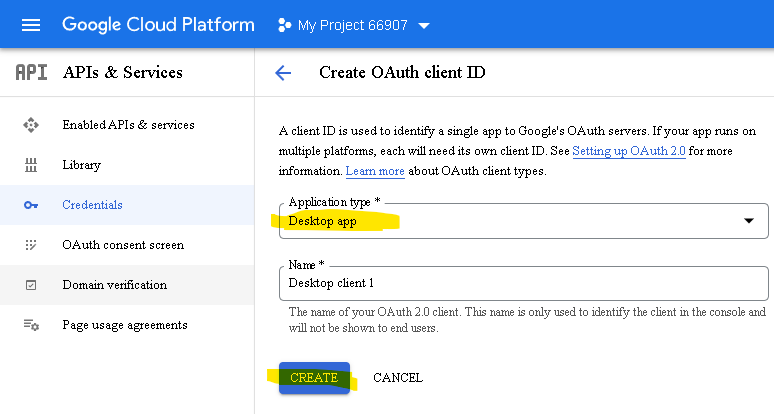
After you’ve registered, copy the “Client ID” and “Client secret” values, which you’ll need later:
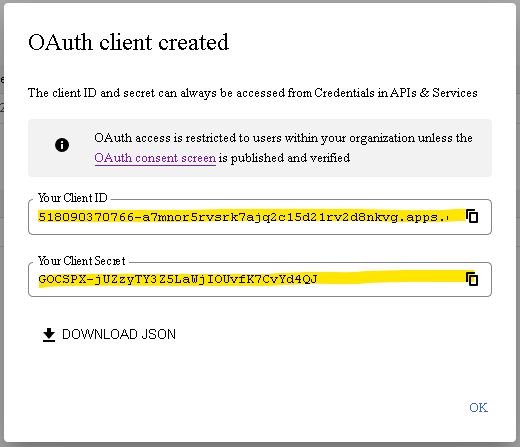
Now we can define clientID, clientSecret and scope variables, as well as Google OAuth 2.0 server addresses. Scope basically specifies what services we want to have access to. In our case it is user’s email address and IMAP/SMTP access:
const string clientID = "12345.apps.googleusercontent.com";
const string clientSecret = "XXXYYY111";
AuthorizationServerDescription server = new AuthorizationServerDescription
{
AuthorizationEndpoint = new Uri("https://accounts.google.com/o/oauth2/auth"),
TokenEndpoint = new Uri("https://oauth2.googleapis.com/token"),
ProtocolVersion = ProtocolVersion.V20,
};
List<string> scope = new List<string>
{
GoogleScope.ImapAndSmtp.Name,
GoogleScope.UserInfoEmailScope.Name
};
Obtain an OAuth 2.0 access token
As we are using installed applications scenario we’ll use NativeApplicationClient class.
Because of a small issue in DotNetOpenAuth we can not use UserAgentClient directly. NativeApplicationClient inherits UserAgentClient and workarounds this issue. You can find the implementation of NativeApplicationClient on the bottom of this article.
NativeApplicationClient consumer = new NativeApplicationClient(server, clientID, clientSecret);
Uri userAuthorizationUri = consumer.RequestUserAuthorization(scope);
Process.Start(userAuthorizationUri.AbsoluteUri);
We are using Process.Start here, but you can also embed WebBrowser control in your application.
At this point user is redirected to Google to authorize the access:
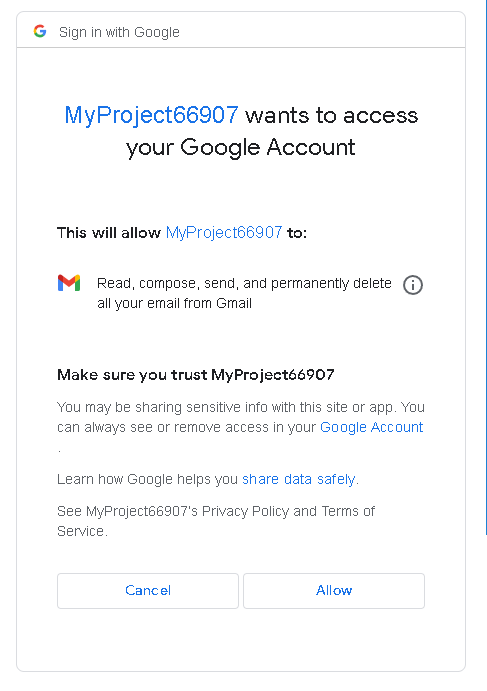
As OOB addresses are no longer supported, to receive the authorization code using this URL, your application must be listening on the local web server. This is the recommended mechanism for obtaining the authorization code.
When your app receives the authorization response, for best usability it should respond by displaying an HTML page that instructs the user to close the browser and return to your app.
Your application needs to create a server that listens on this local address:
http://127.0.0.1:port or http://[::1]:port or http://localhost:port
Query your platform for the relevant loopback IP address and start an HTTP listener on a random available port. Substitute port with the actual port number your app listens on.
In our example we’ll use http://127.0.0.1/auth2callback address.
After this step user is presented a code that needs to be pasted to your application:
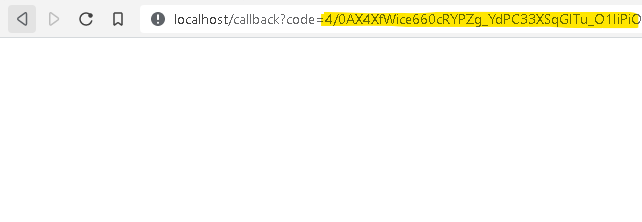
Please note that this code also appears in the title of the browser:
- It is possible to monitor processes on your machine and act automatically when it is there.
- If you use embedded WebBrowser control in your application, you can monitor the HTML document title after any redirect.
Following is a code that reads this code and contacts Google to exchange it for a refresh-token and an access-token:
string authCode = Console.ReadLine();
consumer.ClientCredentialApplicator = ClientCredentialApplicator.PostParameter(clientSecret);
IAuthorizationState grantedAccess = consumer.ProcessUserAuthorization(authCode);
string accessToken = grantedAccess.AccessToken;
An access token is usually valid for a maximum of one hour, and allows you to access the user’s data. You also received a refresh token. A refresh token can be used to request a new access token once the previous expired.
Access IMAP/SMTP server
Finally we’ll ask Google for user’s email and use LoginOAUTH2 method to access Gmail’s IMAP server:
GoogleApi api = new GoogleApi(accessToken);
string user = api.GetEmail();
using (Imap imap = new Imap())
{
imap.ConnectSSL("imap.gmail.com");
imap.LoginOAUTH2(user, accessToken);
imap.SelectInbox();
List<long>; uids = imap.Search(Flag.Unseen);
foreach (long uid in uids)
{
var eml = imap.GetMessageByUID(uid);
IMail email = new MailBuilder().CreateFromEml(eml);
Console.WriteLine(email.Subject);
}
imap.Close();
}
NativeApplicationClient class
The OAuth 2.0 client for use by native applications. It’s main purpose is to build a generic URL containing the auth code, because DotNetOpenAuth library only allows parsing an URL as a method of retrieving the AuthorizationState.
/// <summary>
/// The OAuth2 client for use by native applications.
/// This is a partial implementation which should be used until
/// the feature has been fully implemented in DotNetOpenAuth.
/// </summary>
public class NativeApplicationClient : UserAgentClient
{
/// <summary>
/// Represents a callback URL which points to a special out of band page
/// used for native OAuth2 authorization. This URL will cause the authorization
/// code to appear in the title of the window.
/// </summary>
/// <remarks>
/// See http://code.google.com/apis/accounts/docs/OAuth2.html
/// </remarks>
public const string OutOfBandCallbackUrl = "http://127.0.0.1/auth2callback";
/// <summary>
/// Initializes a new instance of the <see cref="UserAgentClient"/> class.
/// </summary>
/// <param name="authorizationServer">The token issuer.</param>
/// <param name="clientIdentifier">The client identifier.</param>
/// <param name="clientSecret">The client secret.</param>
public NativeApplicationClient(
AuthorizationServerDescription authorizationServer,
string clientIdentifier,
string clientSecret)
: base(authorizationServer, clientIdentifier, clientSecret)
{
}
/// <summary>
/// Initializes a new instance of the <see cref="UserAgentClient"/> class.
/// </summary>
/// <param name="authorizationServer">The token issuer.</param>
public NativeApplicationClient(
AuthorizationServerDescription authorizationServer)
: this(authorizationServer, null, null)
{
}
/// <summary>
/// Creates the URL which should be used by the user to request the initial
/// authorization. Uses the default Out-of-band-URI as a callback.
/// </summary>
/// <param name="scope">Set of requested scopes</param>
/// <returns>URI pointing to the authorization server</returns>
public Uri RequestUserAuthorization(IEnumerable<string> scope)
{
var state = new AuthorizationState(scope);
state.Callback = new Uri(OutOfBandCallbackUrl);
return RequestUserAuthorization(state, false, null);
}
/// <summary>
/// Uses the provided authorization code to create an authorization state.
/// </summary>
/// <param name="authCode">The authorization code for getting an access token.</param>
/// <param name="authorizationState">The authorization. Optional.</param>
/// <returns>The granted authorization, or <c>null</c> if the authorization was null or rejected.</returns>
public IAuthorizationState ProcessUserAuthorization(
string authCode,
IAuthorizationState authorizationState)
{
if (authorizationState == null)
{
authorizationState = new AuthorizationState(null);
authorizationState.Callback = new Uri(OutOfBandCallbackUrl);
}
// Build a generic URL containing the auth code.
// This is done here as we cannot modify the DotNetOpenAuth library
// and the underlying method only allows parsing an URL as a method
// of retrieving the AuthorizationState.
string url = "http://example.com/?code=" + authCode;
return ProcessUserAuthorization(new Uri(url), authorizationState);
}
/// <summary>
/// Uses the provided authorization code to create an authorization state.
/// </summary>
/// <param name="authCode">The authorization code for getting an access token.</param>
/// <returns>The granted authorization, or <c>null</c> if the authorization was null or rejected.</returns>
public IAuthorizationState ProcessUserAuthorization(string authCode)
{
return ProcessUserAuthorization(authCode, null);
}
};
Refreshing access token
An access token is usually short lived and valid for a maximum of one hour. The main reason behind this is security and prevention of replay attacks. This means that for long-lived applications you need to refresh the access token.
Your refresh token will be sent only once – don’t loose it!
We recommend storing entire IAuthorizationState object received from NativeApplicationClient.ProcessUserAuthorization method call. This object contains both: refresh token and access token, along with its expiration time.
The process of refreshing access token is simple:
IAuthorizationState grantedAccess = ...
consumer.RefreshAuthorization(grantedAccess, TimeSpan.FromMinutes(20));
In the example above the access token will not be refreshed if its remaining lifetime exceeds 20 minutes.
Retrieving lost refresh token
When your application receives a refresh token, it is important to store that refresh token for future use. If your application loses the refresh token, it will have to re-prompt the user for consent before obtaining another refresh token.
You’ll need to add approval_prompt=force to your parameters:
AuthorizationServerDescription authServer = new AuthorizationServerDescription
{
AuthorizationEndpoint =
new Uri("https://accounts.google.com/o/oauth2/auth?access_type=offline&approval_prompt=force"),
...
};