Create code signing certificate
Management summary
- You generate certificate signing request on your machine (using certmgr or ActiveX component).
- Private/public key pair is generated along with the request (on your machine).
- You export certificate that represents the request from your certificate key store.
- You extract private key from the certificate that represents the request.
- You send the request (it contains public key only) to CA (or ActiveX does this automatically).
- CA sends your certificate back (crt file that is basically your public key, signed with CA’s keys).
- Finally you need to combine the private key and the crt to create a pfx, that contains both private key and the certificate.
Important points
- Private key is generated along with the certificate request.
- Private key is generated on your machine.
- Private key is never sent to CA (Certificate Authority).
- Certificate received from the CA (*.crt file) doesn’t contain your private key.
- Common name – Your business or organization’s name
- Organization – Your business or organization’s name
- Locality – Your business or organization’s address
- State – The state where your business or organization resides
- Country – The country where your business or organization resides
Generate CSR & private key – ActiveX
Some vendors, like Comodo, use Active X component, that runs on your machine and creates certificate request along with private/public key pair generation on your machine:
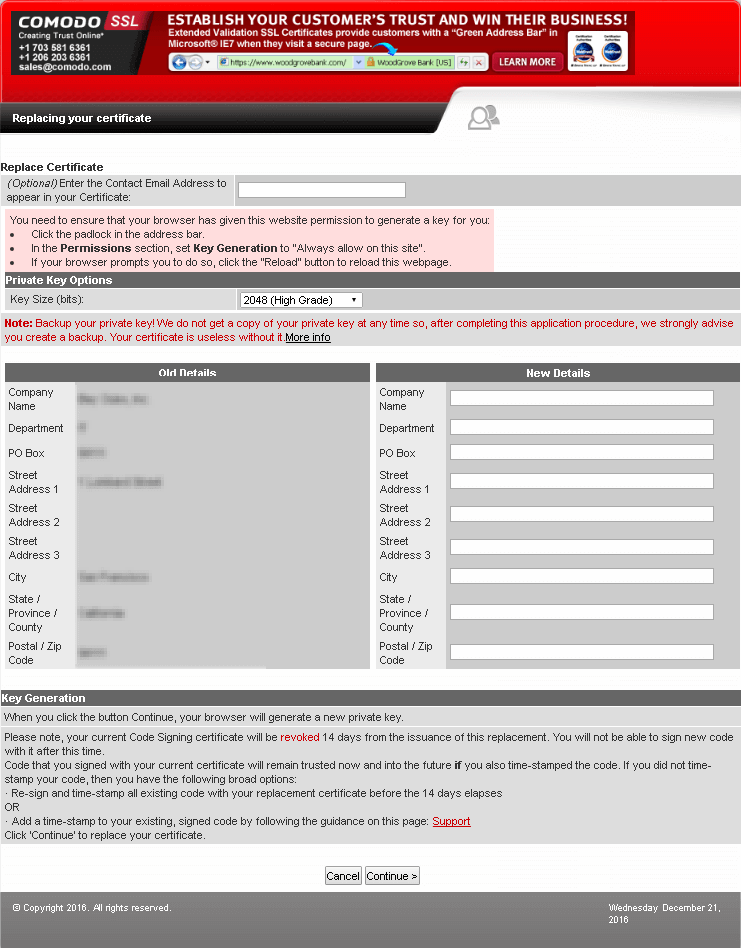
Private key can be found in the certmgr of the local account (not machine’s):
Later on it must be exported as a pfx (e.g. “Request.pfx”).
Generate CSR & private key – CertMgr
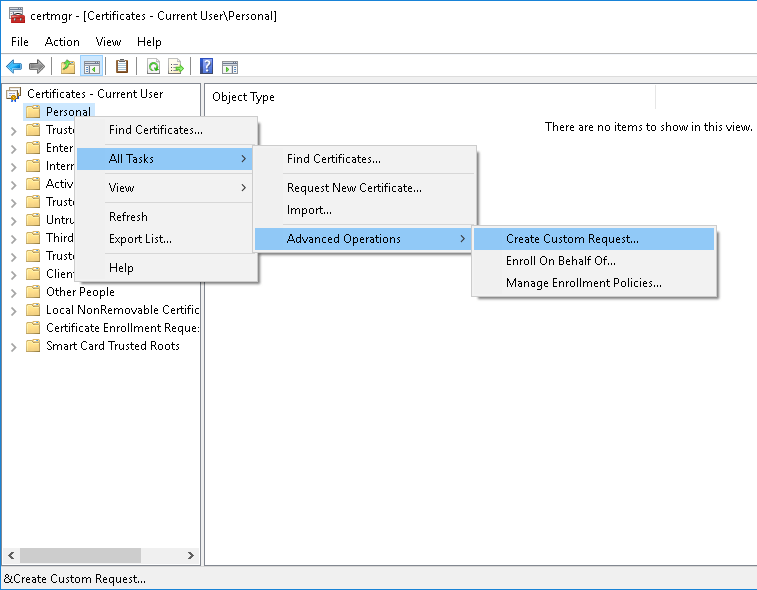
In MMC (certmgr), expand Certificates (Local Computer) and then Personal.
Right-click Certificates, and then go to the following menus: All Tasks > Advanced Operations > Create Custom Request:
Click Next:
Click Next:
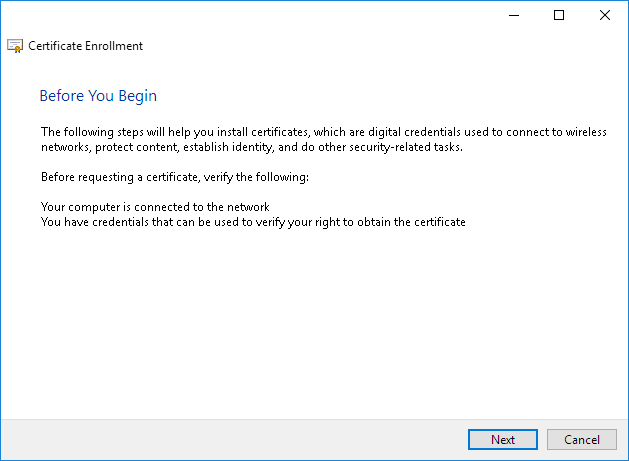
Click Next:
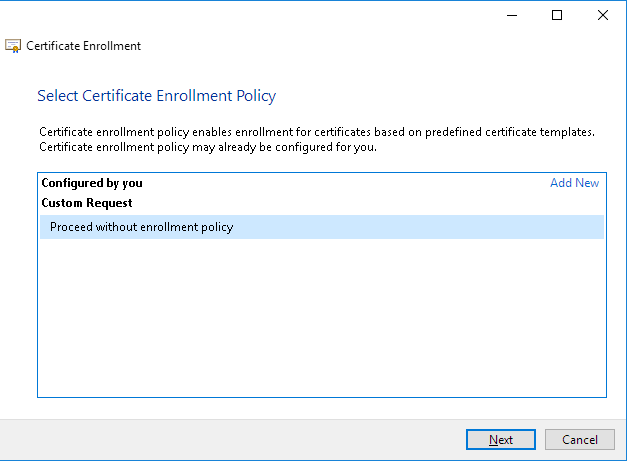
Ensure the Request format is PKCS #10, and then click Next:
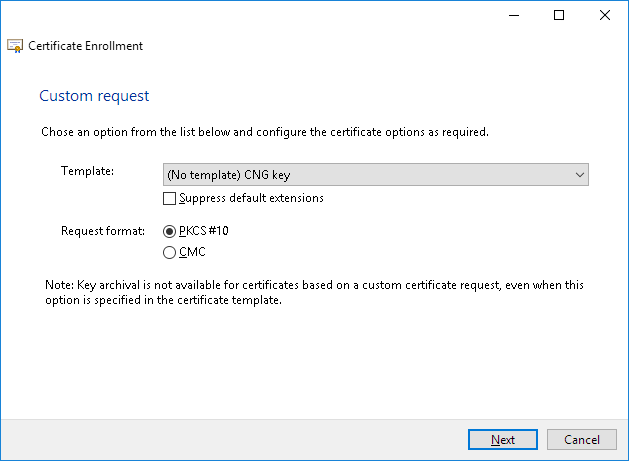
Click the downward-facing arrow next to Details, and then click Properties.
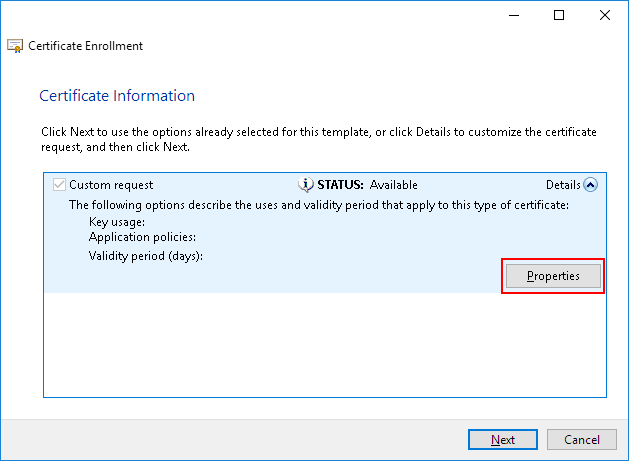
On the subject type, select the following values, enter the corresponding Value, and then click Add:
Go to the Private Key tab, click Key type, and then select Make private key exportable:
Click OK, and then click Next:
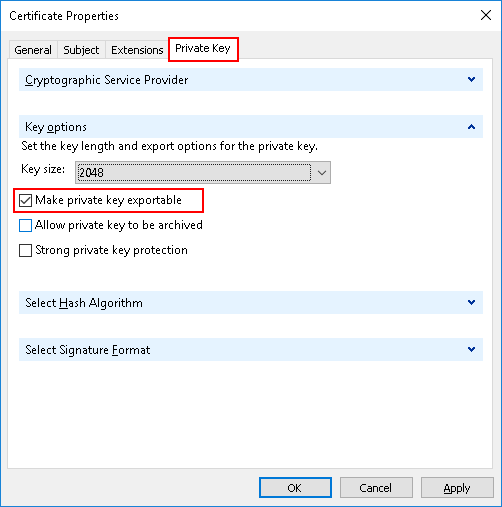
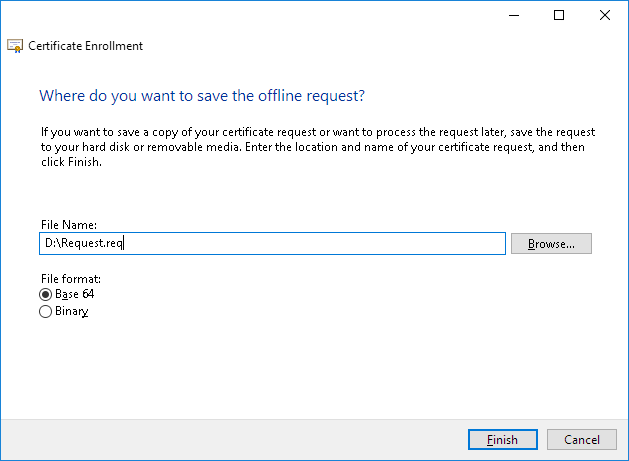
Browse for the location where you want to save the file, enter a File Name (“Request.csr”), and then click Finish.
Your CSR is now stored in the file you saved it to on your local machine.
Request file is regular text file:
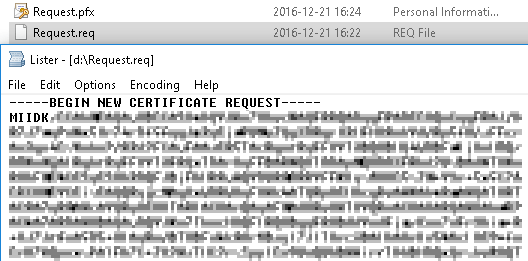
This process also creates a private key, which you will need to use later to create a PFX file to sign your code or driver.
Export certificate that represents the request
If you were using ActiveX to generate certificate request, certificate that represents the request (including private key) is stored in certmgr of the local account (not machine’s):

Go to “Certificate Enrollment Requests”/ “Certificates” (Hit refresh if it is empty):
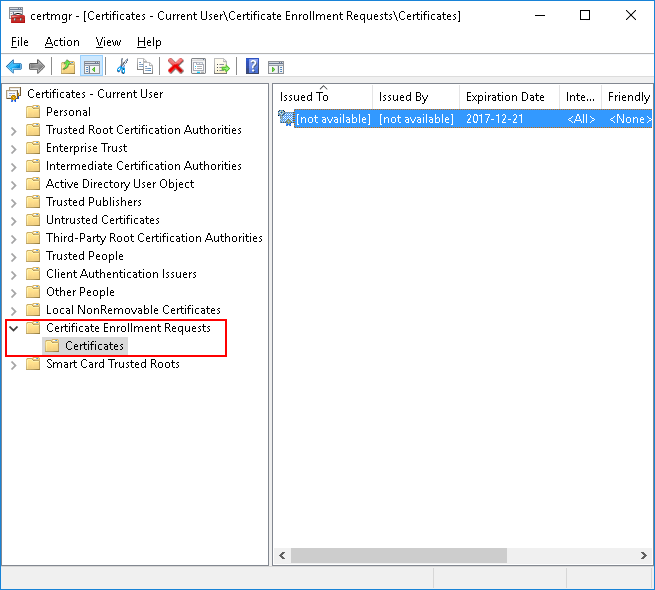
Right-click the certificate and then go to the following menus: All Tasks > Export:
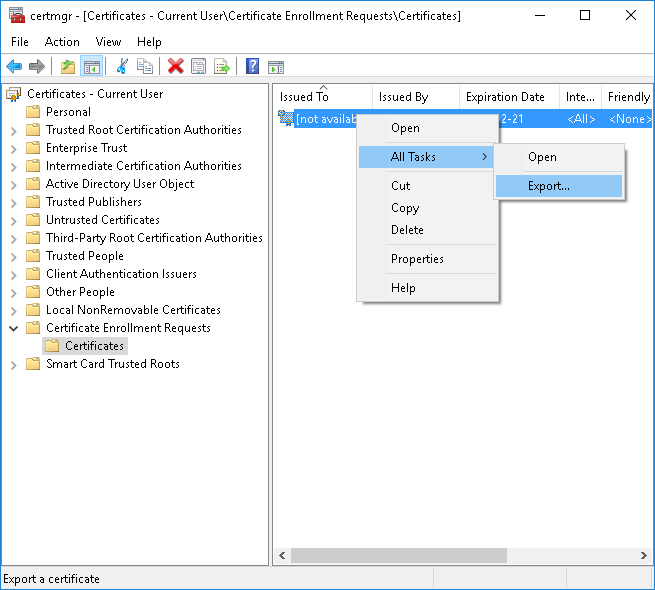
Select export private key and hit Next:
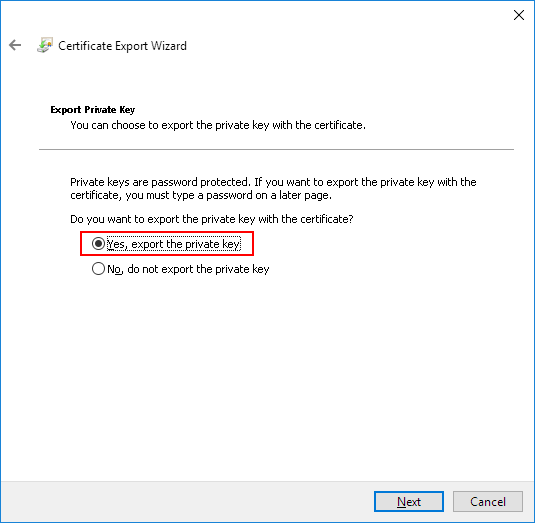
Ensure the Request format is PKCS #12, and then click Next:
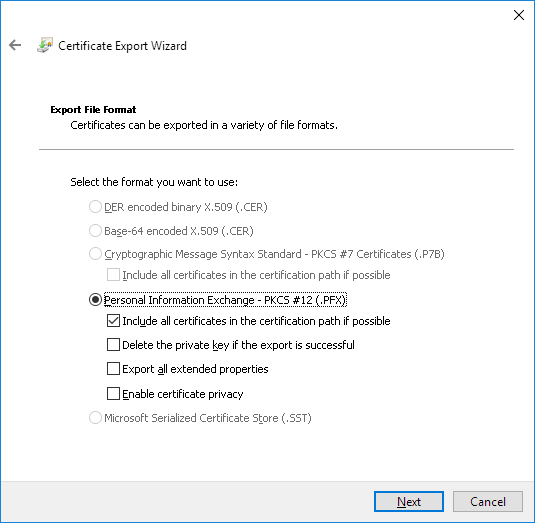
Specify password:
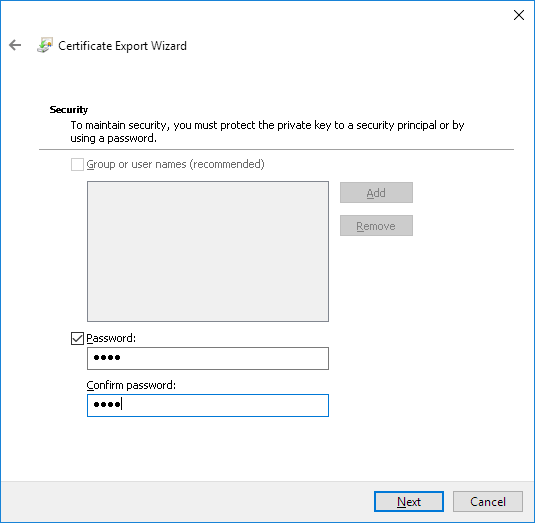
Browse for the location where you want to save the file, enter a File Name (“Request.pfx”), and then click Finish.
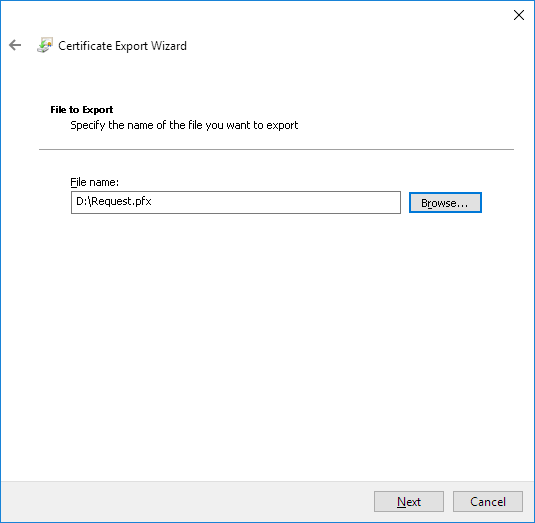
Click Finish:
Certificate that represents your request is now stored in the file you saved on your local machine. It contains both private and public key.
Extract private key
First you’ll need to install OpenSSL.
To extract private key from the request, issue following command:
openssl pkcs12 -in Request.pfx -out Request_PrivateKey.pem -nocerts -nodes
nocerts = private key only,
nodes = no password
Generate CSR & private key – OpenSSL
You can use following command to create certificate request and key using OpenSSL:
openssl req -new -newkey rsa:2048 -nodes -keyout Request_PrivateKey.key -out Request.csr
You may need to convert to convert the key (BEGIN PRIVATE KEY) to PKCS#1 format (BEGIN RSA PRIVATE KEY):
openssl rsa -outform pem -in Request_PrivateKey.key -out Request_PrivateKey.pem
CA creates a certificate
Now you should upload -or- copy&paste request file (“Request.csr”) to your CA, and in return, they should create the certificate for you:
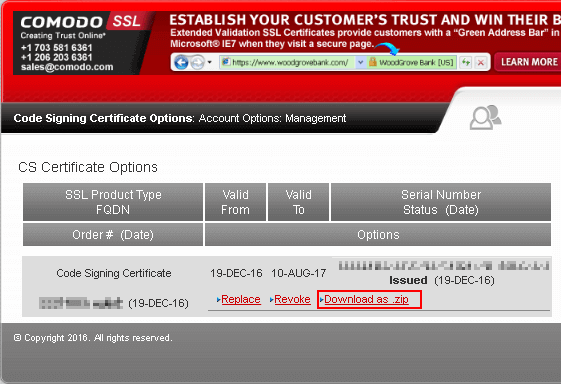
What you receive from your CA looks more or less like this:
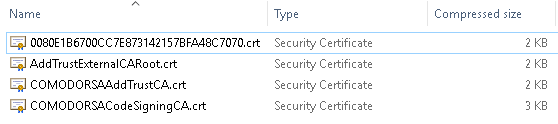
Most important file is the crt file which contains your certificate (it includes public key only).
Combine private key with cert to create pfx
To combine private key from the request and certificate from CA into one pfx certificate, issue following command:
openssl pkcs12 -inkey Request_PrivateKey.pem -in 00…70.crt -export -out 00…70.pfx
The pfx file you created contains both private key and the certificate and can be used to sign your code.