Problem
After the installation of the October 8, 2019 — KB4517389 or KB4520003 or KB4519998 or KB4519990 update (depending on OS version), all TLS encrypted data connections to the affected FTP servers fail.
Error you may see is: “TLS session of data connection has not resumed or the session does not match the control connection”
Detailed explanation
In FTP protocol, data connection does not directly authenticate the client.
Client uses control connection to authenticate, then it established data connection using PASV command followed by the STOR (upload) or RETR (download) command.
The server opens a port and waits for the client to connect to it and upload/download files.
An attacker could figure out the port the server listens to, connect to it before the client, and upload a piece of malware.
TLS session resumption prevents this. It acts as a form of authentication. If the TLS session of the data connection matches the session of the control connection, both the client and the server have the guarantee, that the data connection is genuine. Any mismatch in sessions indicates a potential attack.
Ftp.dll library uses .NET’s SslStream that relies on Schannel (Microsoft Secure Channel – a security package that facilitates the use of Secure Sockets Layer (SSL) and/or Transport Layer Security (TLS))
Cause
The KB4517389 addresses the following issue:
“Addresses an issue in security bulletin CVE-2019-1318 that may cause client or server computers that don’t support Extended Master Secret (EMS) RFC 7627 to have increased connection latency and CPU utilization. This issue occurs while performing full Transport Layer Security (TLS) handshakes from devices that don’t support EMS, especially on servers. EMS support has been available for all the supported versions of Windows since calendar year 2015 and is being incrementally enforced by the installation of the October 8, 2019 and later monthly updates.”
It looks like Schannel stared enforcing EMS. If the server runs a TLS stack which is not compatible with this change, the FTP data connection fails.
OpenSSL, which is used by most servers, supports EMS since version 1.1.0 (released 25th August 2016).
Affected Servers
- All FTP servers using OpenSSL older than version 1.1.0
- FileZilla Server (all versions). The latest version uses an insecure/outdated OpenSSL version 1.0.2.11 from 2017.
Solution
Contact the server administrator, explain the situation and and request an upgrade of the FTP server software and of the installed OpenSSL version.
As a temporary workaround, the KB4517389 (or equivalent for non-Windows 10 machines) can be uninstalled.
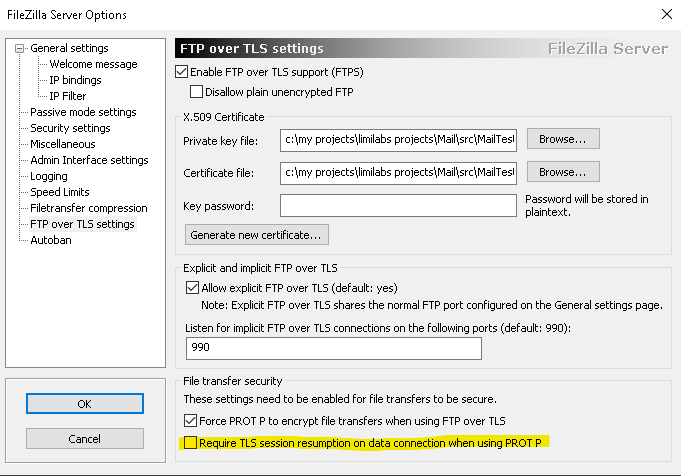
As a temporary workaround on FileZilla server you can go to “FileZilla Server Interface/Edit/Settings/Ftp over TLS setting” and uncheck “Require TLS resumption on data connection when using FTP over TLS”: